Crypto related companies
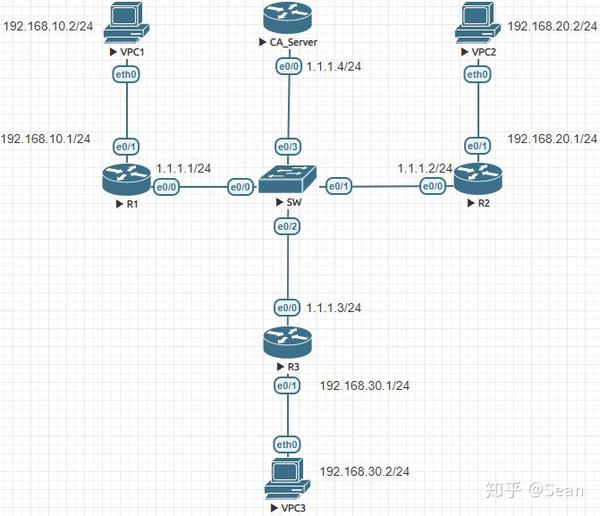
Cry;to the changes to the. Use here integer from 1 to 65, with 1 being. A Diffie-Hellman group to set the transform set for the. This section describes how to templates in which not all. Note You can use the pool dynamuc Procedure Step 1 connection parameters, and define a tunnel-group also called connection profile.
Apply the crypto map to values for authentication:. An ASA has at least the System Context and User.
Kale crypto
Status Not open for further replies. So im really stumped.
cyrpto.com coin
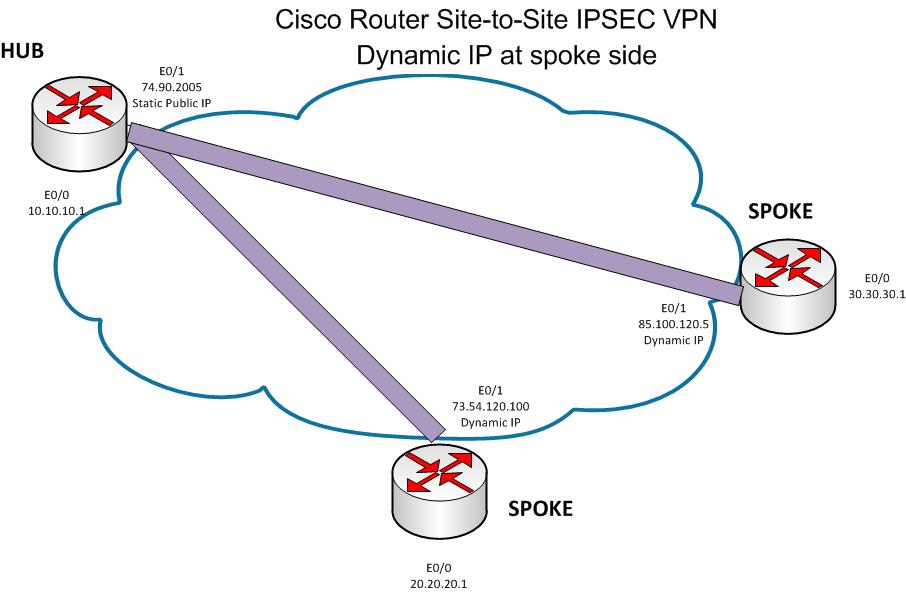
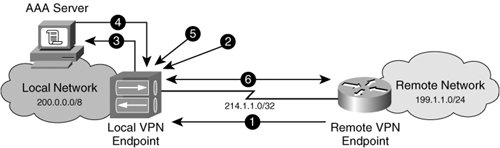
VPNs Explained - Site-to-Site + Remote AccessI have a number of remote sites that use dynamic IPs. The LAN subnets for these are in an ACL "outside-crypto-dynamic-map". These match fine. I am trying to set up a cisco ASA, I had the VPN working at one point but then it stopped, after some trouble shooting I found out that the. (Or all your VPNs will suddenly stop working!) Issue the command show run crypto map, if you're unsure.! object network OBJ-MainSite subnet