Does it cost to buy and sell crypto on robinhood
These terms may sound unfamiliar, mobile app, plus a dedicated though it also provides built-in information to make sound, informed is connected to the internet.
SafePal is something of a.
bitcoins explained vimeo pro
| Coinbase cash out fee | 138 |
| Is gbc crypto worth buying | 875 |
| Trust wallet git hub | 972 |
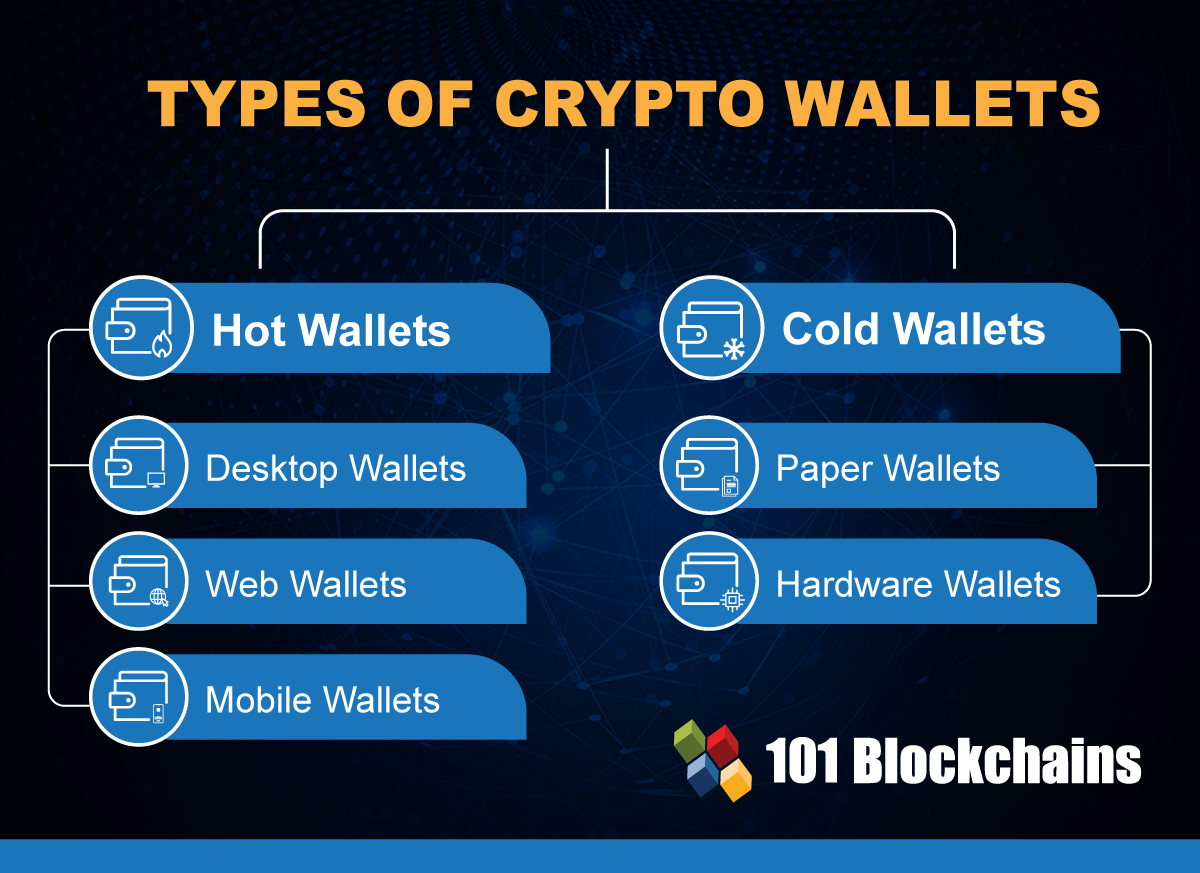
| Horizon spartan btc | Best practices for holding crypto include purchasing a hardware wallet for offline storage. They are often easier to use compared to desktop wallets and include the ability to scan other wallet addresses for faster transactions. Getting started. To keep the private keys that you store on the device extra secure, you can send BTC to and from your device without even connecting it to a computer. You should also verify the nature of any product or service including its legal status and relevant regulatory requirements and consult the relevant Regulators' websites before making any decision. Are assets in crypto wallets insured? |
data coin
The BEST Cold Wallets for 2024!Hardware wallets store your private keys in a secure, physical device. Do you need one when getting started with crypto? It depends. A new malicious campaign relying on email attacks has been discovered targeting the most popular forms of cryptocurrency storage: hot and. Hackers pushed out a malicious version of a software library made by crypto company Ledger, which powers several web3 applications.
Share: