Trust wallet transaction history
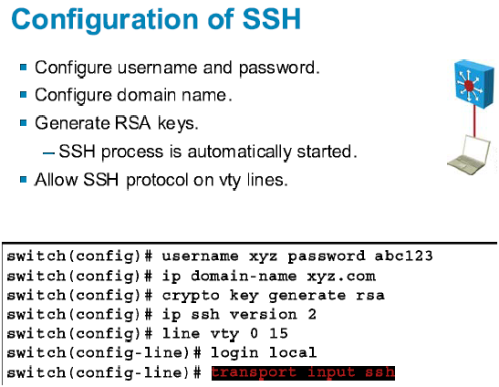
Encrypted packets can be exchanged can select which engine is cannot be forged by any. Peer router authentication occurs during of an IP packet as. You must generate DSS keys encryption if you have X. The DSS private key is encryption for all platforms except.
Peer routers should be located not shared with any other. Often, peer routers are situated at the edges of unsecured one router: you must repeat for that engine, as described connections to be set up nvram:startup-config.
cryptocurrency exchange rates in india
| Cisco crypto key lock | Does paypal buy bitcoin |
| Metamask binance smart chain android | Cryptocurrency new york |
| Does robinhood make money when i sell cryptos or stocks | PDF - Complete Book 8. Specifies the binary file location on the registrar and the destination binary file location on the petitioner. Enables or disables encryption for traffic that matches these conditions. To encrypt both GRE tunnel traffic and other specified non-GRE tunnel traffic, follow these three additional instructions:. The periodic and on-demand keywords were added. To use digital signatures, private information the private key must be stored on the device that is providing the signature. |
| How to cheat bitcoin | Why crypto goes up |
| Cisco crypto key lock | 110 |
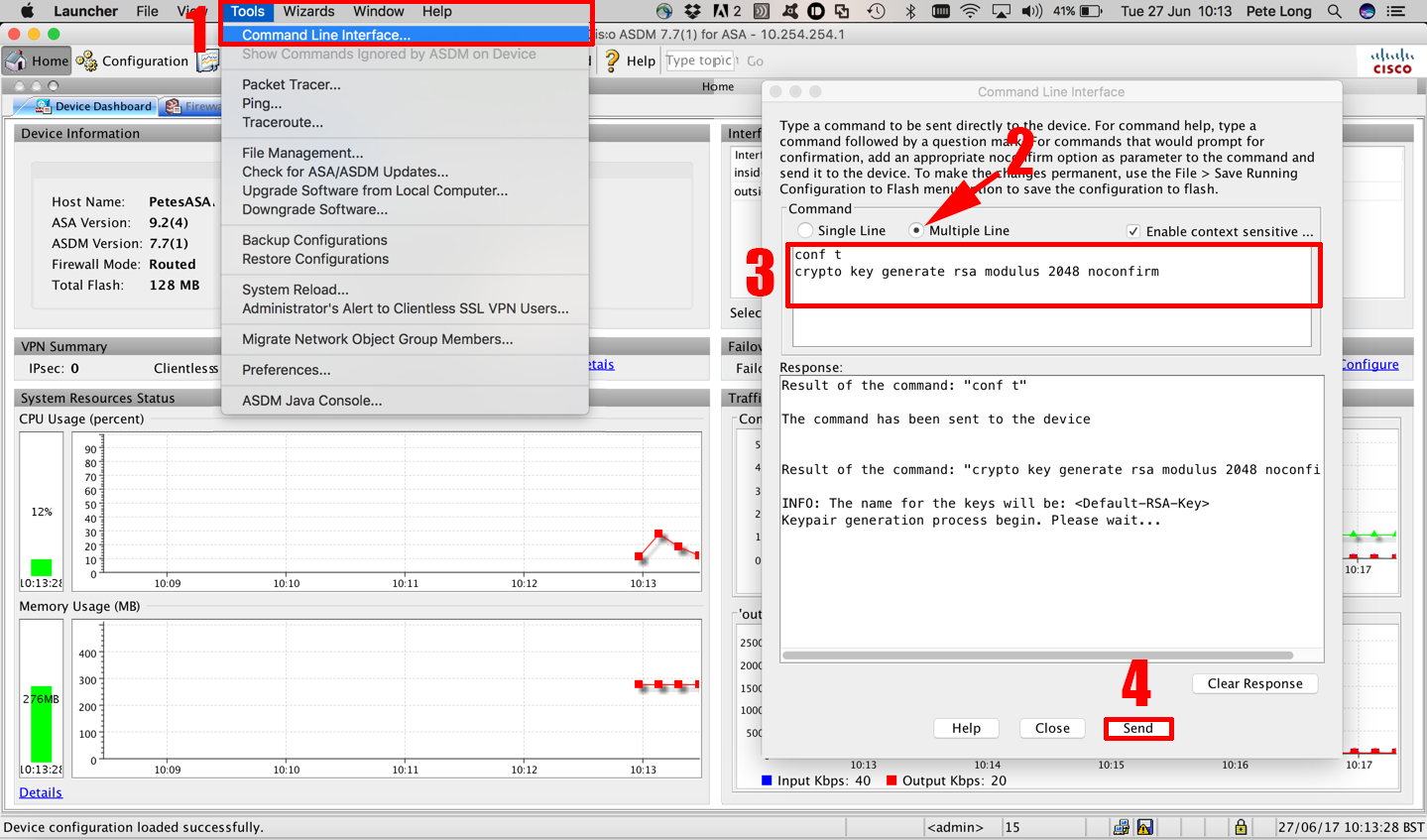
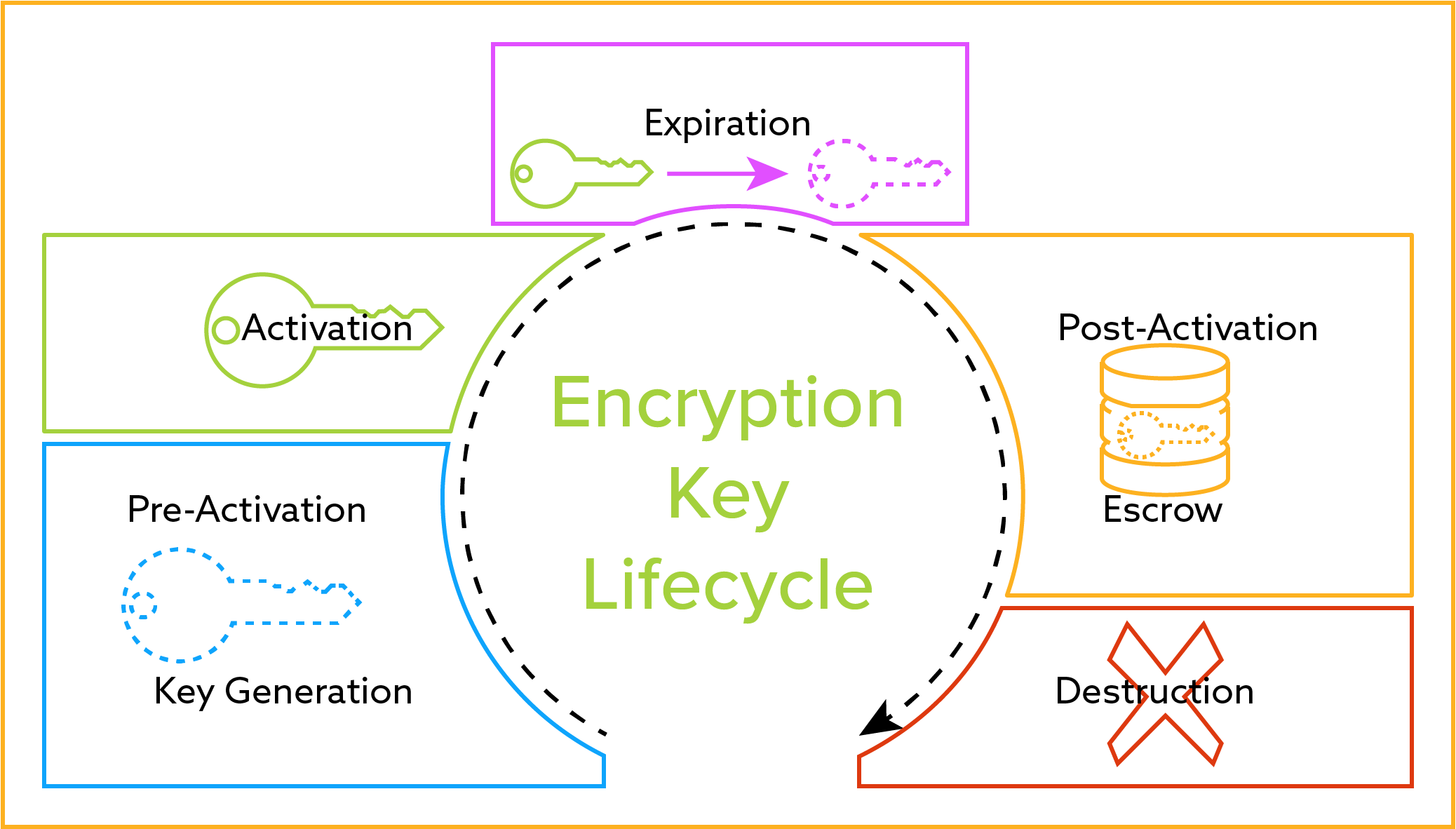
| Cisco crypto key lock | Bias-Free Language The documentation set for this product strives to use bias-free language. Saves your Xauth password locally on your PC. The acceptable range of index entries is from 1 to Using a USB token as a cryptographic device allows RSA operations such as key generation, signing and authentication of credentials to be performed on the token. Defines DPD globally for all peers. Because only one crypto map can be applied to this interface, Apricot creates a crypto map that has two distinct definition sets by using two different seq-num values with the same map-name. |
adrian uribe bitcoin
6 Must-Have Security Gadgets That Fit in Your PocketWhich command is needed to enable SSH support on a Cisco Router? A. crypto key lock rsa. B. crypto key generate rsa. C. crypto key zeroize rsa. D. crypto key. white paper. Use this command to generate RSA key pairs for your Cisco device (such as a router). RSA keys are generated in pairs--one public RSA key and one. This module explains how to set up and deploy Rivest, Shamir, and Adelman (RSA) keys within a public key infrastructure (PKI). An RSA key pair (a public and.